Authored by:
- Doron Rotman, Managing Director, Technology Assurance – Audit, KPMG LLP
- Maksim Vander, Managing Director, Technology Assurance – Audit, KPMG LLP
- Christopher Montone, Director, Technology Assurance – Audit, KPMG LLP
- Ruixiang Wu, Director, Technology Assurance – Audit, KPMG LLP
Companies are facing cyberattacks every day, with large organizations across industries reporting hackers gaining access to customer information, taking down IT systems and often making demands for ransom payments. As cyberattacks become more frequent and sophisticated, organizations are facing increased stakeholder calls and regulatory requirements to show they are protecting their information appropriately. According to a recent KPMG survey[1], 83% of companies suffered a cyberattack in the past year, and respondents said it took them an average of one month to fully contain the attack.
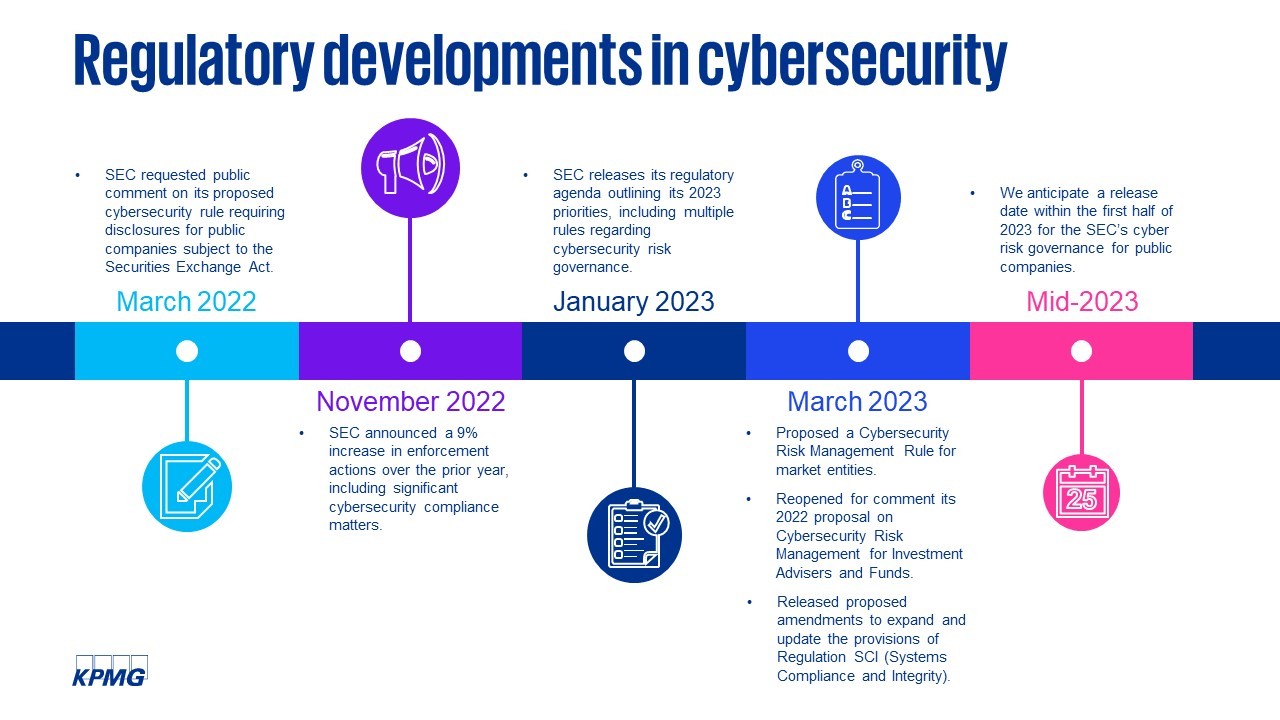
The Securities and Exchange Commission (SEC) is undertaking a comprehensive effort to increase cybersecurity preparedness and resilience for all registrants. This spring, new cybersecurity reporting requirements[2] for public companies are expected, enhancing and standardizing risk management, strategy, governance and incident disclosures. The SEC also released proposed cybersecurity rules for broker-dealers and other market entities[3] and opened comments on rules for registered advisers and funds[4] in March 2023. At the same time, the SEC is enforcing large penalties against some companies for misleading disclosures around past cyberattacks. Additionally, in April 2023, the Public Company Accounting Oversight Board listed cybersecurity among its top priorities for this year’s inspections.[5]
With the increased focus on cybersecurity from regulators, customers and investors, executives have a growing responsibility to understand their company’s cyber risks and the state of cyber programs. As a baseline, with oversight from the board, management should be preparing now to comply with the SEC’s final rules on cybersecurity disclosures. Going beyond regulatory compliance, it’s imperative to understand how your organization is positioned to detect, mitigate and remediate any cybersecurity threats and vulnerabilities with respect to information systems as well as business continuity and overall cyber incident reliance.
You are here: Assessing your organization’s current cyber risk
As a first step, management should evaluate the organization’s current situation, laying the groundwork for a strategy for enhancing the organization’s cyber maturity, achieving SEC compliance and reassuring customers, investors and other stakeholders that appropriate safeguards are in place. Key questions may include:
- Does management understand how mature the organization’s cyber programs are in relation to others in the same industry?
- Is there appropriate insight into the current and future business, regulatory and compliance impacts of cyber risks on the organization’s supply chain, both upstream and downstream?
- Has any risk assessment been performed to understand how the organization may be impacted by the current or future SEC proposals and regulations?
Third-party assessments and attestations are tools for management and the board to understand the organization’s current cyber readiness and respond to stakeholder demand for transparency. A cyber maturity assessment is a way for the financial reporting and internal controls function to get a clear, easily digestible view of the organization’s current cyber program benchmarked against other organizations of similar size and industry. A cybersecurity-focused SOC report can provide attestation for cyber controls.